Category CyberSecurity
AI Workflow Automation

When it comes to choosing a phone system for your business, one of the biggest decisions you’ll face is whether to use softphones or deskphones. Both options allow your team to make and receive calls — but how they do it (and what they cost) can vary significantly.
Vulnerability Scan

Learn how vulnerability scans detect security flaws, assess risk levels, and help you fix issues before hackers can exploit them. Protect your business today.
Softphone
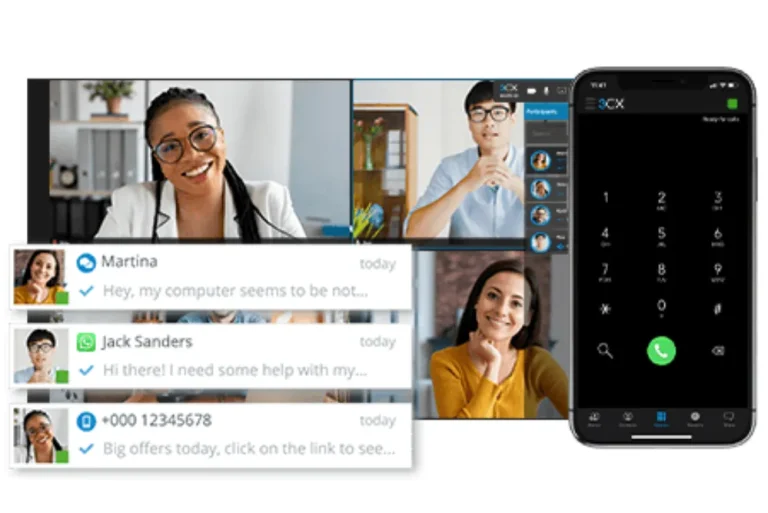
When it comes to choosing a phone system for your business, one of the biggest decisions you’ll face is whether to use softphones or deskphones. Both options allow your team to make and receive calls — but how they do it (and what they cost) can vary significantly.
SMB1001

Think cyberattacks only hit big companies? Think again. SMBs are now the #1 target — and most breaches come down to easy-to-fix gaps. SMB 1001 shows you how to protect your business without being an IT expert.
Dark Web Credential Scan

A Dark Web Credential Scan helps you find out if your credentials are out in the wild—so you can secure your business before someone lets themselves in.
How to improve business communication systems

pgrade to a smarter, more reliable solution and watch your business communication thrive... Your business deserves better than outdated, unreliable communication.
What is PIM and PAM? A Simple Guide

What is PIM and PAM? A Simple Guide
Protecting your business doesn’t have to be complicated.
With PIM and PAM, you can secure your systems like a pro.
Building Business Resilience

How Managed Services Drive Business Resilience and Ensure Success Through Any Challenge
DMARC DKIM and SPF – what are they and why do I need them?

Email is the lifeblood of business communication, but it’s also a prime target for cyber threats. When it comes to email security, DMARC, DKIM, and SPF are your secret weapons. DMARC, DKIM, and SPF—are three security measures designed to defend…
The Ultimate Cyber Security Guide: Small Business Survival Tactics and Managed Security Bundles

Small Business Survival Tactics and Managed Security Bundles, The Ultimate Cyber Security Guide
