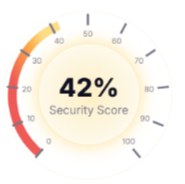
Vulnerability Scan
Learn how vulnerability scans detect security flaws, assess risk levels, and help you fix issues before hackers can exploit them. Protect your business today.
How Vulnerability Scans Work

Vulnerability scans are an essential part of keeping your business IT secure, yet many small businesses either overlook them or don’t run them often enough.
A vulnerability scan works like a car service.
It’s a quick, automated check-up that looks under the hood of your business technology to spot weaknesses you might not see day-to-day. These could include outdated software, misconfigured settings, or open ports that could give cybercriminals an easy way in.
When done regularly, vulnerability scanning helps you catch problems early, before they become costly breaches. In this guide, we’ll explain what a vulnerability scan is, how it works, and why it’s a smart first step in strengthening your cyber security.
Even better — it ticks a key requirement for SMB:1001 Level 1, helping small businesses take that first step towards better security.
Let’s take a closer look at how a vulnerability scan works and what it actually checks for behind the scenes.
What is vulnerability scan?
A vulnerability scan is an important part of your business’s cyber security toolkit.
It’s a simple, automated check that looks across your systems – including computers, servers, networks, and cloud tools – to identify weaknesses that cybercriminals could exploit.
Think of it like a regular service for your IT: It helps you find and fix issues before they turn into costly problems. By running regular vulnerability scans, you can:
Identify missing security updates that should have been installed
Detect outdated software with known vulnerabilities
Find misconfigured settings that could leave systems exposed
Spot default usernames or passwords that are easy to guess
Flag open ports or services that shouldn’t be publicly accessible
Regular scanning keeps your business ahead of potential threats and is a proactive step toward meeting compliance requirements like SMB:1001 Level 1.
Step 1: Finding What’s on Your Network
Before the scan can spot any problems, it first needs to understand what’s actually connected to your network.
This includes physical devices like desktops, laptops, servers, printers, and routers — but also software, cloud tools, and background services that are quietly running in the mix.
Many business owners are surprised at how many devices and systems are discovered — especially if older equipment hasn’t been retired properly, or if new tools have been added without anyone flagging them.
Shadow IT (unauthorised apps or devices) is more common than you’d think.
Think of it like doing a headcount in your office — not just checking who’s there, but also what they’re using and whether they should be there at all.
Getting this clear picture is a crucial first step. You can’t protect what you don’t know you have.
Step 2: Figuring Out What Each System Is Running
Once the scanner knows what’s on your network, it takes a closer look at what each device is actually running behind the scenes — things like the version of Windows or macOS, the apps installed, the type of server software, and more.
This matters because older software or outdated versions often have known flaws that hackers actively look for.
Even a small version difference — like 2.1 vs 2.3 — can be the difference between a secure system and one that’s vulnerable to attack.
It’s a bit like checking which cars in your fleet are due for a service — some might look fine, but under the bonnet, they’re overdue for critical updates.
By understanding the exact version and setup of each system, the scan can match it against a global database of known threats and flag anything that’s out of date or potentially risky.

Where are your hidden security gaps?
Run a quick vulnerability scan and see what hackers could exploit before it’s too late.
Step 3: Spotting the Risks That Matter
Now that the scan knows what devices you have and what they’re running, it gets to work checking for known security issues — the kinds that cybercriminals actively look for.
It does this by comparing your systems against global databases of vulnerabilities, including:
- Vendor-specific advisories from companies like Microsoft, Cisco, and others
These databases are updated constantly with details about security flaws in software and devices. If your business is using a program or version that’s flagged in one of these lists, the scan will catch it.
Here’s what it’s looking for:
- Missing security updates or patches
- Known vulnerabilities, like Log4j or EternalBlue – tools hackers already know how to exploit
- Weak or default passwords that haven’t been changed
- Open ports that expose your systems to the internet when they shouldn’t
- Misconfigured settings, like a website that accidentally shows its file directories
👉 Each issue it finds is matched to an official vulnerability ID (called a CVE) and given a severity rating – so you know which problems are low-risk and which need urgent attention.
This step gives you the “why it matters” part of the scan – not just what’s out there, but what’s actually putting your business at risk right now.
Step 4: What’s included in a vulnerability scan report?
When a vulnerability scan detects a problem, it doesn’t just tell you something’s wrong – it gives you a detailed breakdown so you can understand the risk and take action quickly.
A typical vulnerability scan report will include:
Name of the vulnerability – e.g. OpenSSL Heartbleed or Outdated Apache Version – this identifies the exact security issue.
CVE ID (Common Vulnerability Identifier) – every known vulnerability is assigned a global ID (e.g. CVE-2023-1234) linking to detailed technical information.
Description and risk explanation – a plain-English summary of:
What the issue is
- Why it’s a security risk
- How a hacker could exploit it (e.g. gaining access, crashing systems, stealing data)
Severity score (CVSS) – a standardised score that ranks each issue from low to critical, helping you prioritise urgent fixes.
What’s affected – details of the specific software, service, or device at risk (e.g. Apache 2.2.15 running on port 80).
Proof and detection evidence – how the scanner identified the issue, such as a server response or security flag.
How to fix it – actionable remediation steps, which might include:
Applying security patches or updates
Changing default usernames or passwords
Disabling or blocking risky services
Links to trusted resources – direct access to vendor instructions, official security bulletins, or best-practice guides.
By giving you both the technical detail and plain-language explanations, vulnerability scan reports make it easier to understand, prioritise, and fix issues before they become real threat
Not sure if your business has hidden risks?
We can run a quick, automated vulnerability scan to uncover weaknesses in your systems — from outdated software to misconfigured settings — and give you a clear action plan to fix them before cybercriminals can take advantage.
Strong cyber security doesn’t have to be complicated or costly.
A vulnerability scan is a straightforward way to protect your systems, demonstrate compliance with standards like SMB:1001, and prove to customers and partners that you take security seriously.
By acting now, you’re not only reducing your risk but also showing leadership in an area many small businesses overlook. That confidence can become a real competitive advantage.
If your business requires virus and security help above, or virus removal beyond this article please call us