SMB1001
Think cyberattacks only hit big companies? Think again. SMBs are now the #1 target — and most breaches come down to easy-to-fix gaps. SMB 1001 shows you how to protect your business without being an IT expert.
Cybersecurity for Small Business: Your No-Jargon Guide to SMB 1001
Cyber threats aren’t just a big business problem anymore.
In fact, small and medium-sized businesses (SMBs) are now the #1 target for cybercriminals.
Why?
Because most attacks exploit basic security gaps — things that are easy to fix but often overlooked.
That’s where SMB 1001 comes in.
This Australian cybersecurity framework was created with everyday businesses in mind.
It gives you a step-by-step approach to securing your systems, protecting your data, and building resilience — without needing a background in IT.
Let’s unpack what it is, why it matters, and how your business can benefit.
What Is SMB 1001?
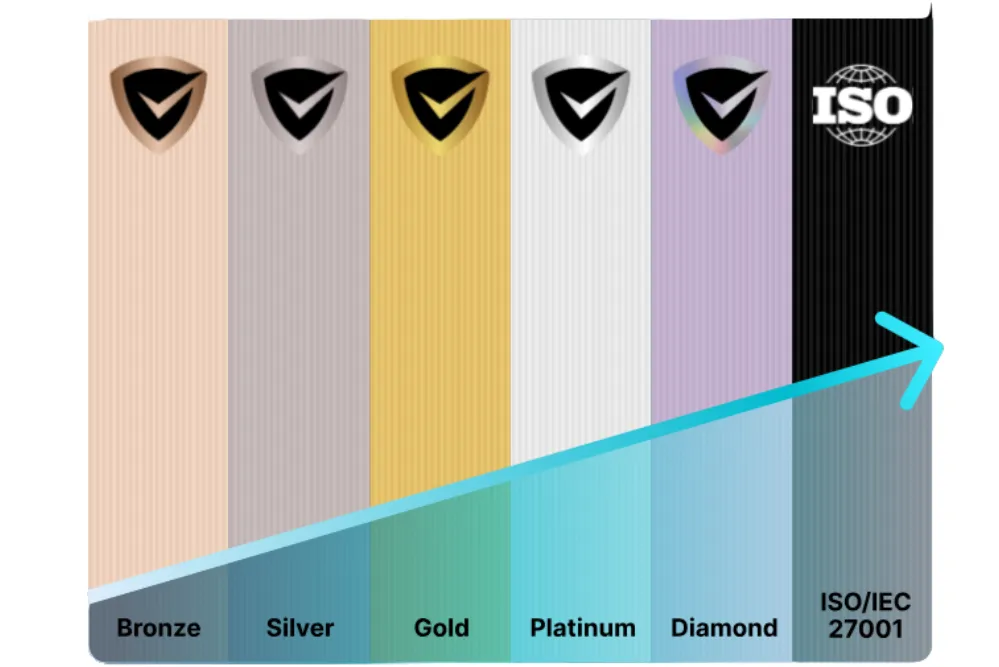
SMB 1001 is a step-by-step roadmap to cybersecurity maturity, tailored for real-world businesses (not just tech companies or big enterprises).
It’s split into five progressive levels, each one building on the last — so you don’t have to fix everything overnight.
Levels 1 to 3 are self-assessed, helping you lay strong foundations and build internal capability.
Levels 4 and 5 require external certification to validate your controls and demonstrate a mature, well-managed security posture.
Once certified, you can display an official SMB 1001 badge on your website and materials — giving clients and partners visible proof that you take cybersecurity seriously.
SMB 1001 is also a strong precursor to ISO 27001 — it gets your systems and mindset ready for formal certification, which involves annual audits and full recertification every five years.
More and more small businesses are adopting SMB 1001 to win client trust, meet compliance needs, and future-proof their cybersecurity — without the overwhelm.
Whether you’re a sole trader or managing a national team, the SMB 1001 framework helps you:
Strengthen Cyber Defences
Minimise Business Disruptions
Safeguard client data and trust
Comply with Legal and Industry standards
Level 1
Level 1 of the SMB 1001 framework focuses on cyber hygiene — the essential, everyday practices that form the backbone of your cybersecurity.
These are the simple things that stop most attacks in their tracks.
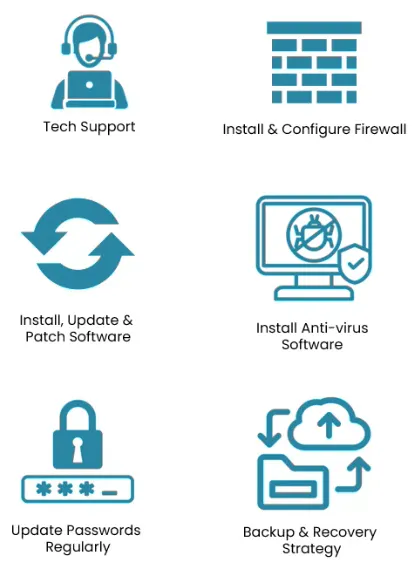
Unique Passwords
Weak or reused passwords are one of the biggest security risks for small businesses. If a hacker gets hold of one password, they can often access multiple systems.
Level 1 requires that every user and every system has a unique, complex password — no more “admin123” or using your dog’s name for everything.
We recommend using business-grade password managers to create and store strong credentials securely, and enforcing password policies across your team.
Updates & Patching
Many cyberattacks target known vulnerabilities — software flaws that already have fixes available but haven’t been installed.
That’s why it’s crucial to keep all your operating systems, apps, and devices updated regularly.
Level 1 requires that all systems receive timely updates, ideally through automated patching tools that minimise disruption and reduce human error.
Backups
No matter how secure you are, accidents happen — from ransomware to hardware failures.
Level 1 requires your business to have automated, routine backups of critical data, stored both onsite and in the cloud.
But it’s not enough to just set and forget — you also need to test your backups regularly to ensure they can actually restore your data when it matters most.
Limited Admin Access
Not everyone in your business needs full control over your systems. In fact, giving too many people administrator-level access is a major security risk. If one of those accounts is compromised — whether through phishing, malware, or misuse — the damage can be catastrophic.
Level 1 of SMB 1001 requires a “least privilege” approach:
Users only get access to the data and tools they need to do their job — nothing more.
Admin rights are reserved for key personnel, and those accounts are monitored closely.
Shared logins and generic admin accounts are phased out to improve accountability and reduce risk.
By limiting admin access, you reduce the potential attack surface and make it much harder for threats to spread across your network.
🔒 It’s not about limiting your team — it’s about limiting the risk.
Firewall Protection
Firewalls act as your business’s first line of defence — controlling what traffic is allowed in and out of your network. Without one, your systems are exposed to unnecessary risk from the internet.
Level 1 requires a properly configured firewall on all internet-facing systems, including routers, servers, and remote access tools.
This means:
Blocking unused or insecure ports
Only allowing traffic from trusted sources
Enabling logging and alerts for unusual activity
Keeping firewall firmware updated
If you’re using a business-grade router, it likely includes basic firewall capabilities — but these still need to be checked, configured, and maintained regularly.
Why It Matters
Skipping the cybersecurity basics is like leaving your front door wide open and hoping no one walks in. It’s not a question of if attackers will try — it’s when. And in most cases, they’re looking for easy wins: businesses that haven’t done the simple things.
The reality is, most cyberattacks aren’t sophisticated. They rely on common weaknesses like weak passwords, missing updates, or overly generous access controls. When those gaps exist, attackers can slip in quietly — often without you knowing until it’s too late.
By taking care of the fundamentals in Level 1:
You block the most common entry points used by cybercriminals
You reduce your exposure to threats like ransomware, phishing, and data theft
You build a solid foundation that makes every future security layer stronger
Think of it like home security: there’s no point investing in security cameras and motion sensors if you’re not even locking the doors.
How We Help You Nail Level 1
As your IT partner, we don’t just tell you what to do — we handle it for you:
✅ Business-grade password management: No more sticky notes or reused passwords
✅ MFA setup across Microsoft 365, email, and cloud apps
✅ Automated updates & patching — no disruptions, no missed fixes
✅ Secure, verified backups (onsite & cloud) that actually restore when needed
✅ Access audits to clean up admin rights and tighten control
💬 “Cybersecurity starts with the fundamentals — we make sure they’re done right from day one.”
Start with the basics. Stop the easy attacks. Build real resilience.
Level 2
Level 2 is all about weaving cybersecurity into the daily rhythm of your business.
It’s not just about tools — it’s about people, processes, and accountability. Here’s how it takes shape:
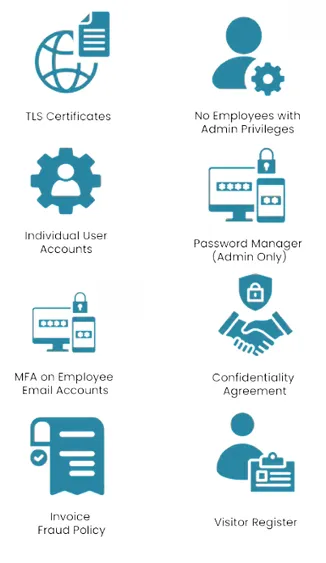
Multi-Factor Authentication (MFA)
Adding MFA is like putting a deadbolt on your digital front door. Even if someone steals a password, they can’t get in without a second verification method — like a code sent to your phone or an app-based prompt.
MFA is required on all critical systems such as email, Microsoft 365, file storage platforms, and remote access tools.
It’s one of the most effective, low-cost ways to prevent unauthorised access.
Clear Policies
Having strong tools in place is great — but without clear, enforceable policies, even the best systems can be misused.
That’s why Level 2 encourages you to develop practical, easy-to-understand policies for:
Password security (e.g. complexity, expiry, and storage rules)
Remote work (how staff connect securely from home or on the road)
Device management (who can use what, and how it should be protected)
We help write these policies in plain English so they’re actually followed — not just filed away and forgotten.
Access Reviews
As businesses grow, it’s easy to lose track of who has access to which systems, files, or data — and old permissions often linger long after someone changes roles or leaves the company.
Level 2 introduces regular access reviews, where we:
Audit existing user access across platforms and tools
Remove unnecessary or outdated permissions
Ensure access is tied to job roles and current responsibilities
This keeps your data locked down, reduces insider risk, and supports compliance with privacy and data security requirements.
Security isn’t just about “keeping the bad guys out” — it’s about ensuring the right people have the right access, at the right time.
Individual User Accounts
Shared accounts might be convenient, but they’re a security risk. If something goes wrong, there’s no way to tell who did what.
Level 2 encourages assigning individual user accounts across all systems so actions are traceable, accountability is clear, and access can be removed immediately when someone leaves.
Confidentiality Agreements
Even the best security systems can’t prevent a breach if someone inside leaks information.
Level 2 recommends having employees and contractors sign confidentiality agreements to clearly outline expectations around sensitive data handling and non-disclosure. This adds a human layer of protection and supports compliance with data privacy laws.
Why it Matters
Technology alone can’t protect your business — especially if you don’t know who’s accessing what, or what’s actually in place.
Level 2 is all about bringing structure and visibility to your IT environment. By introducing individual logins, clear policies, and regular access reviews, you shift from reactive fixes to proactive control.
This means:
You can trace actions back to specific users — no more shared logins or guesswork
Admin rights and data access are tightly aligned to roles and responsibilities
Your systems are supported by enforceable, easy-to-follow policies
Confidentiality is built into your culture with signed agreements
Physical and digital access is documented and auditable
Level 2 lays the groundwork for operational maturity — giving you the tools to stay in control, meet compliance needs, and reduce risk as your business grows.
How We Support You at Level 2
Level 2 is about shifting from “set and forget” to ongoing control. We help you tighten policies, clean up access, and gain full visibility over your IT environment:
✅ Policy development & documentation: We create plain-English policies around passwords, remote work, and device use — so your team knows exactly what’s expected.
✅ Asset tracking setup: We implement tools to monitor devices, software, and system access — so you always know what you have and where it is.
✅ Access audits & reviews: We check who has access to what, clean up old permissions, and align access to roles and responsibilities.
✅ Individual user accounts: We help eliminate shared logins so actions are traceable and access can be removed as soon as someone leaves.
✅ Confidentiality agreements: We provide templates and support to roll out NDAs and data handling agreements across your team.
✅ Physical visitor tracking: We guide you on setting up simple registers to monitor physical access to your workspace.
💬 “Security isn’t just IT’s job — it’s a system of checks, visibility, and clear expectations that keep your whole business protected.”
Level 3
Once your business has mastered the essentials (Levels 1 and 2), it’s time to think bigger.
If you’re scaling fast, handling sensitive data, or working toward certifications, the higher levels of the SMB 1001 framework help you build a more mature, strategic cybersecurity posture.
These levels focus on proactive protection, continuous improvement, and making security a core part of how your business operates.
Level 3 is about moving from ad-hoc security to a more systematic, process-driven approach.
You’ve got the basics down — now it’s time to standardise and strengthen.
Asset Tracking
You can’t protect what you don’t know you have.
Many SMBs don’t have a clear, up-to-date inventory of their IT environment — which means devices get lost, software goes unpatched, and security gaps go unnoticed.
With proper IT asset tracking, you gain visibility over:
All your laptops, desktops, servers, and mobile devices
Installed software, licences, and renewal dates
Where each device is located and who’s using it
This isn’t just about neat records — it’s about staying in control and avoiding security blind spots.
Training Your Team
The majority of successful cyberattacks begin with a human mistake — someone clicking on a fake email, downloading a malicious attachment, or entering credentials into a fake login page.
That’s why ongoing staff training is one of the most powerful defences you can put in place.
We help deliver clear, practical training that empowers your team to:
Recognise phishing attempts, dodgy links, and scam messages
Understand red flags like unexpected password resets or file-sharing requests
Know what to do — and who to tell — if they see something suspicious
When your staff know what to look for, they become your first line of defence.
What it includes:
- Employees learn how to spot red flags — like suspicious links, fake login pages, or unusual requests
Documented policies and procedures for managing security across systems, devices, and users — so everyone is on the same page
Regular vulnerability assessments to identify and fix weak spots before attackers can exploit them
Standardised system configurations that ensure every new device is hardened and aligned with best practices from day one
🛠️ At Level 3, your business isn’t just secure — it’s consistently secure.
Cybersecurity Policy & Incident Response Plan
Strong security isn’t just about having the right tools — it’s about knowing how to use them, and what to do when something goes wrong.
At Level 3, we help you formalise two essential documents:
Cybersecurity Policy: A clear, tailored guide that outlines how your business manages passwords, protects sensitive data, handles remote work, and secures devices. It sets expectations for staff and ensures consistency across your systems.
Incident Response Plan: A step-by-step action plan for what to do in the event of a cyberattack, phishing attempt, or data breach — including who to notify, how to contain the threat, and how to recover safely.
Together, these documents turn cybersecurity from an informal habit into an organised, business-wide process — so you can respond quickly, confidently, and compliantly when the unexpected happens.
Secure Disposal of Devices & Documents
Security doesn’t stop at your screen — it also applies to what’s sitting in your storage cupboard or heading for the bin.
At Level 3, we help you implement proper disposal practices for both physical and digital materials that could expose sensitive data:
Devices: We ensure laptops, phones, and other hardware are fully wiped and securely disposed of or recycled — so no leftover data falls into the wrong hands.
Documents: We help set up clear policies for securely shredding printed materials like invoices, HR files, or client records.
Secure disposal reduces the risk of accidental data leaks, supports your privacy obligations, and keeps your business safe — even after the equipment or paperwork is gone.
What Comes After: Levels 4 to 5 (And When to Level Up)
Level 4
At this stage, cybersecurity becomes data-driven and proactive. You’re not just reacting to issues — you’re reviewing, improving, and building resilience across every layer of your IT environment.
What Level 4 includes:
✅ Advanced MFA across critical systems — including email, RDP, cloud apps, VPNs, and access to digital assets.
✅ Secure remote access controls — to ensure remote work is protected through VPNs and strict credential management.
✅ Vulnerability scanning — regular checks of your public-facing systems to spot weaknesses before attackers do.
✅ Backup & recovery for digital assets — with tested plans to restore critical data and systems quickly.
✅ Audit logging and monitoring — to detect suspicious activity and support forensic investigation if needed.
✅ Incident response & review — don’t just fix issues — learn from them and adapt.
✅ Cybersecurity awareness training — more than the basics; staff are trained on current threats and attack tactics.
✅ Cyber insurance readiness — meet insurer requirements with documented policies and protections.
✅ Specialist support — access to expert cybersecurity guidance, not just general IT help.
💬 “You can’t improve what you don’t measure — and Level 4 gives you the tools to do both.”
Level 5
This is the platinum standard of cybersecurity.
At Level 5, security isn’t just a policy or a checklist — it’s part of how your business runs, makes decisions, and evolves. Cybersecurity is fully integrated into your business culture, from executive planning to frontline workflows.
What Level 5 includes:
✅ Proactive threat detection
Including regular penetration testing, active threat hunting, and the use of AI or analytics to detect anomalies before damage is done.
✅ Security embedded into business processes
Cybersecurity considerations are built into vendor selection, onboarding, system design, and product delivery.
✅ A culture of continuous improvement
Your team reviews and tests systems regularly — learning from incidents, refining plans, and staying ahead of threats.
✅ MFA everywhere
Multi-Factor Authentication is enforced across all business accounts, employee emails, VPN, RDP, and access to sensitive digital data.
✅ Application control
Only approved apps are allowed to run, reducing the risk of malware or unauthorised software.
✅ Data encryption at rest
Critical data is encrypted to protect it even if physical devices or storage are compromised.
✅ Macro blocking
Microsoft Office macros are disabled to prevent malicious document-based attacks.
✅ Up-to-date digital asset register
Your inventory of systems, devices, and apps is continuously updated to reflect real-time changes.
✅ Supplier and third-party risk management
A digital trust framework ensures partners, cloud services, and vendors meet your security standards.
✅ Admin vetting
IT administrators undergo police checks or formal screening processes to minimise insider risk.
✅ Tested incident response plans
Response plans aren’t just written — they’re rehearsed, reviewed, and improved based on real-world scenarios.
💬 “At this stage, your business is resilient, agile, and ready for anything.”
Who Are These Levels For?
Levels 4 to 5 are ideal for businesses that:
Are experiencing rapid growth or managing multiple sites
Handle financial, health, or customer-sensitive information
Need to comply with regulatory or industry standards like the Essential Eight, ISO 27001, or APRA CPS 234
Are working with enterprise clients or government
You’re Not in This Alone
You don’t need a full-time IT department to get secure.
With the right support, even the smallest team can build strong cyber foundations.
We help you:
- Assess your current risks
- Get compliant with SMB 1001
- Create a clear, affordable path to higher levels as your business grows
✅ Final Word: Start Smart, Stay Secure
Cybersecurity can feel complex — but ignoring it is riskier than ever.
The SMB 1001 framework gives you a clear, manageable path to protect your business from real-world threats. Start with the essentials, build confidence, and grow into more advanced practices when you’re ready.
Ready to find out where you Stand?
Let’s assess your current cybersecurity level and create a simple action plan.
Whether you’re starting from scratch or levelling up, we’re here to help you secure what matters most.